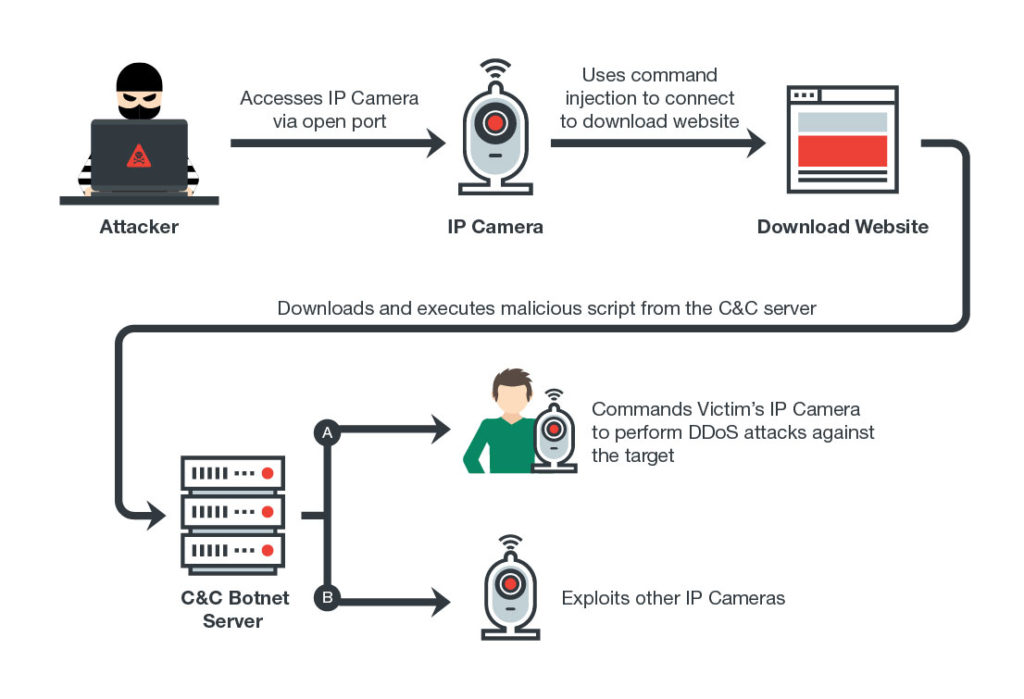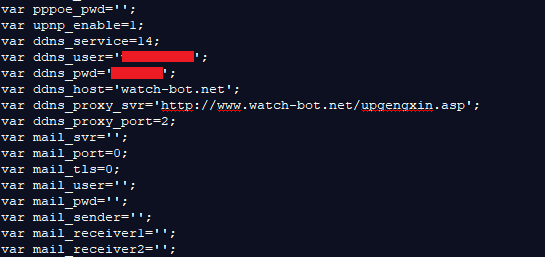
GitHub - 649/Netscraped-Exploit: Framework for obtaining all the credentials stored in vulnerable Netwave IP cameras. Can be used to break into IP cameras, use for research only.
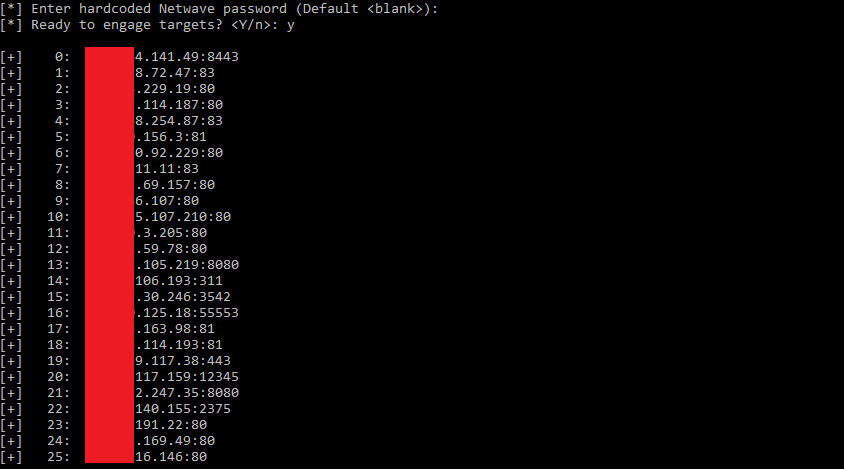
GitHub - 649/Netscraped-Exploit: Framework for obtaining all the credentials stored in vulnerable Netwave IP cameras. Can be used to break into IP cameras, use for research only.

Sasuke Ourad on X: "Netwave .. IP cam That leaks your credentials and WIFI password .. Enjoy IOT ^_^ https://t.co/GBu8jPRkiq" / X







![Exploit a Router Using RouterSploit [Tutorial] - YouTube Exploit a Router Using RouterSploit [Tutorial] - YouTube](https://i.ytimg.com/vi/u0YrWfze9es/hqdefault.jpg)