Building secure systems with PII Data Protection Techniques — Part I | by priyadarshan patil | inspiringbrilliance | Medium

Classifying and tagging PII fields residing in BigQuery and automating access control to them. | Google Cloud Blog

Your introduction to personally identifiable information: What is PII? - Analytics Platform - Matomo

Premium Vector | Personally identifiable information pii personal data storage and identification cyber security confidentiality regulation flat vector illustration






.svg)

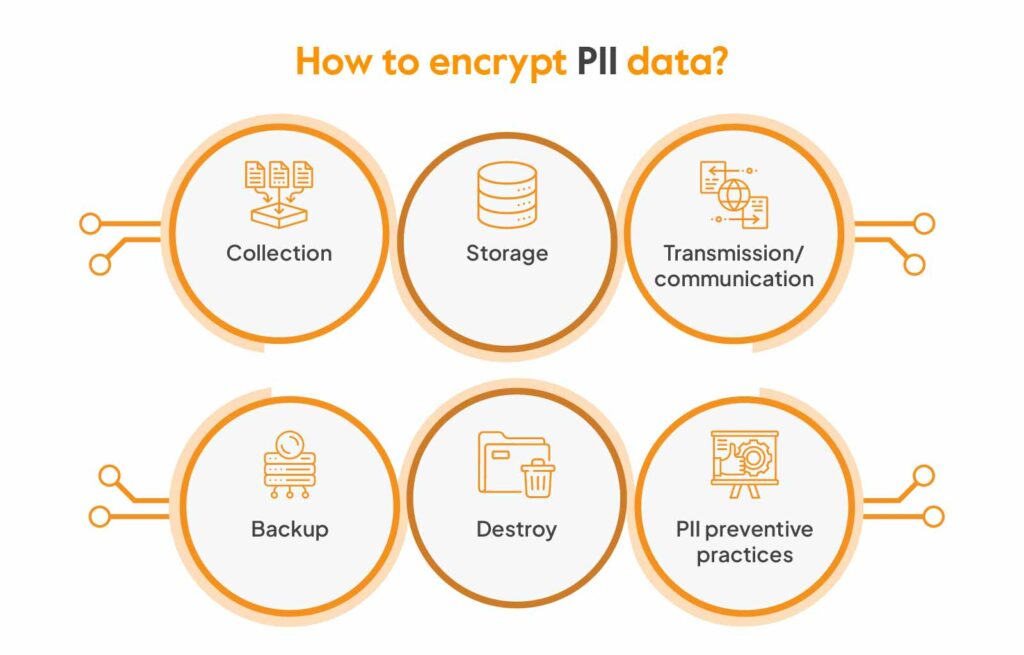

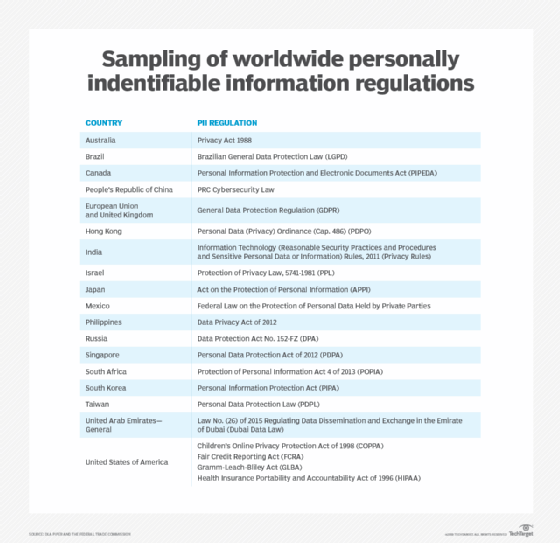
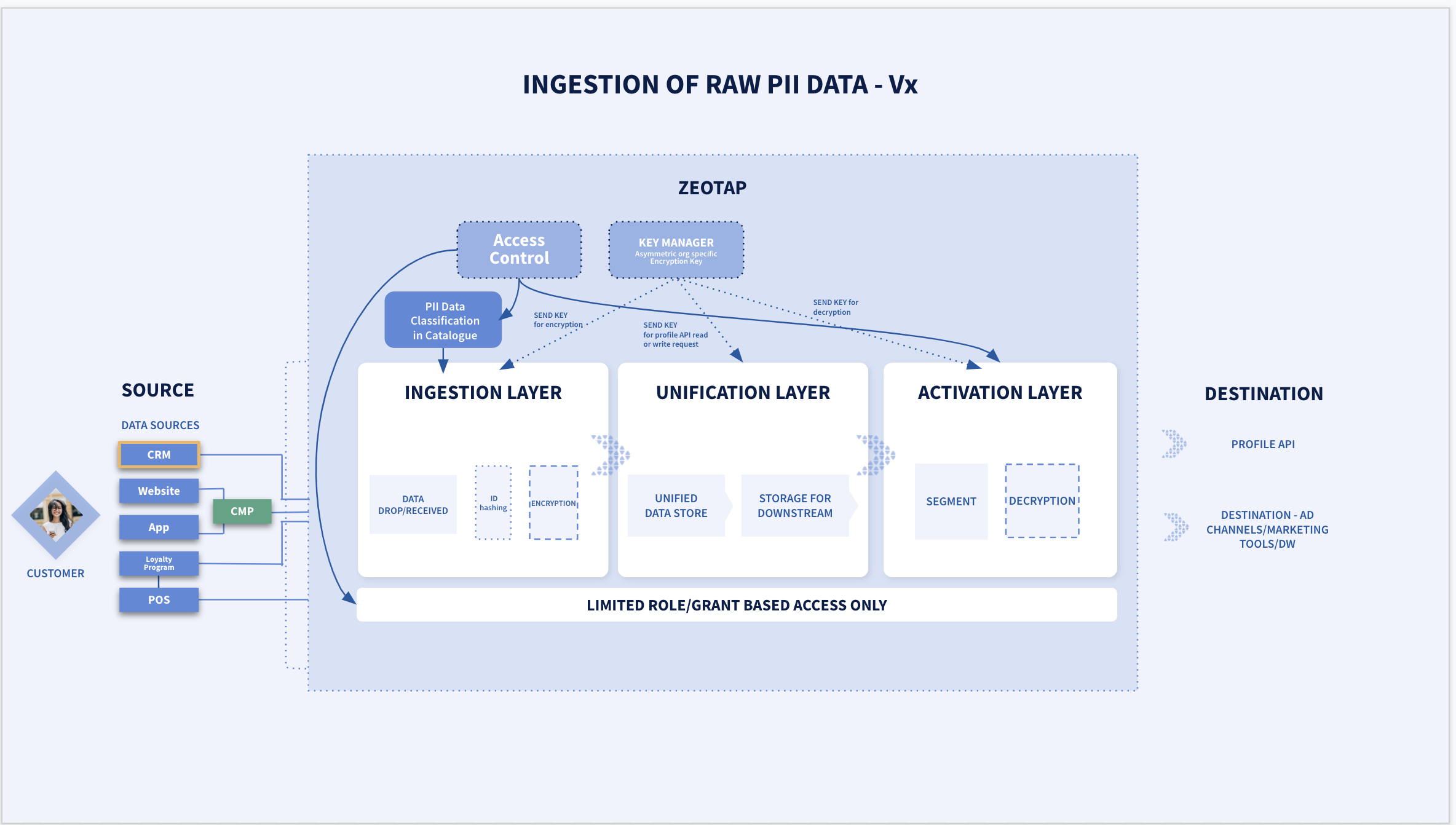
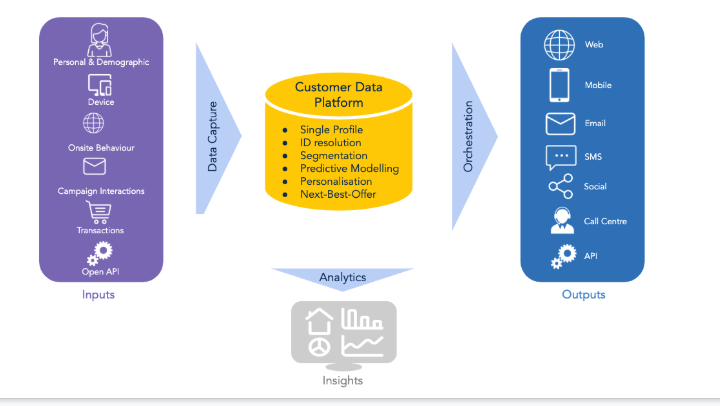

:max_bytes(150000):strip_icc()/Personally-identifiable-information-pii_final-f413d282a7b74142b147720a77811659.png)